|
I then added them to Dennis's FGPA cracker page. You can see this here:
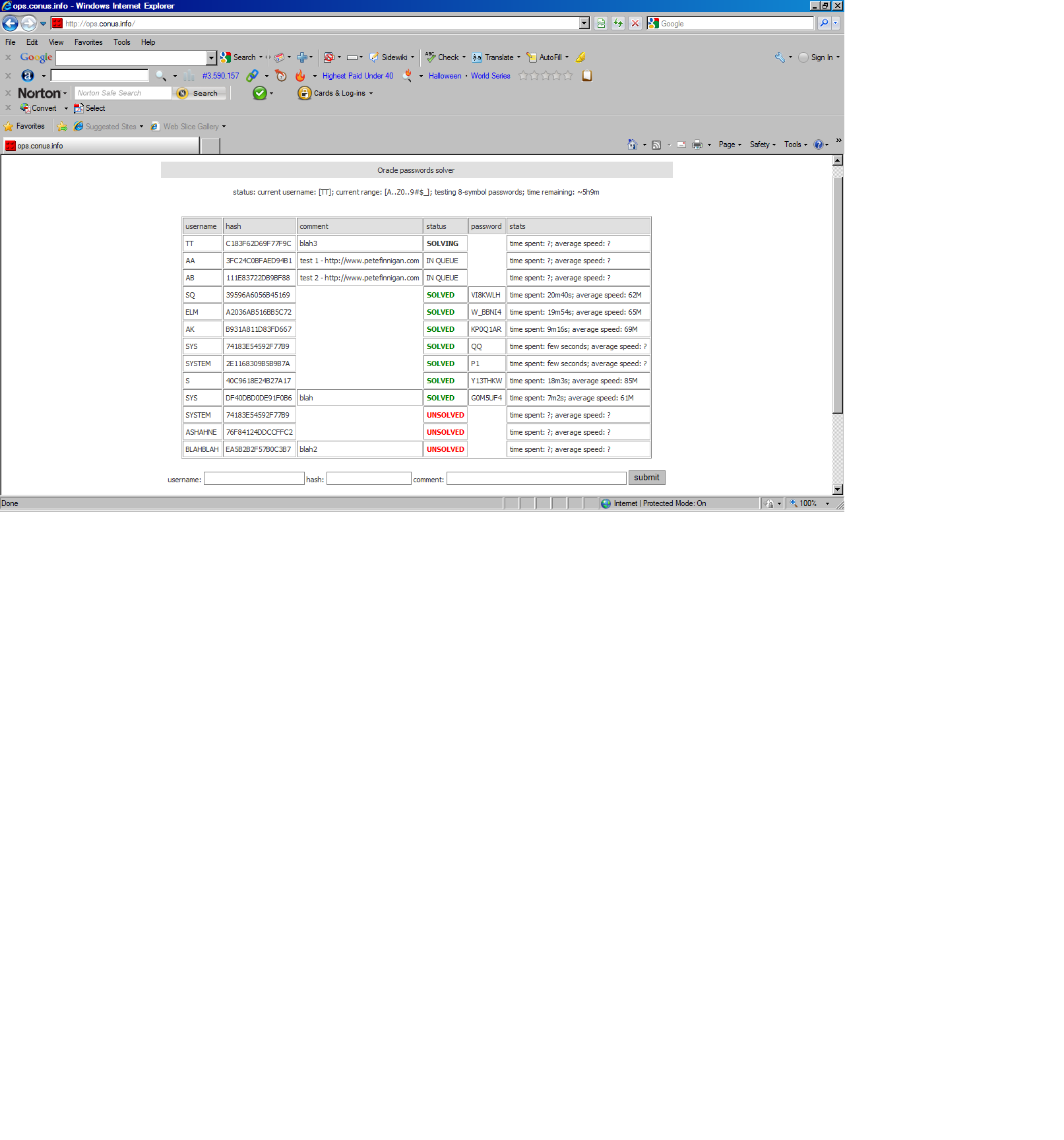
I had created two tests before looking at the screen and as there is now another test running that has 3 or so hours left i didnt want to now wait before blogging. I deliberately created the two sample users above with passwords starting at "A" and "Z" because I wanted to test whether the password choice has an effect on the time to crack. From the screen dump above it would seem that this will be the case. When mine finish I will know for sure. From the output above it seems that passwords starting later in the alphabet take more than 15 minutes and those earlier in the alphabet around 10 or less.
There should be a possible improvement that could be made to the algorithm of Dennis's cracker that requires some math and statistics calculations to be made. If passwords generally have a skew towards starting with certain characters more than others then there will be a benefit in start choice for the cracker or in randomizing the journey through the brute force choices. If passwords for instance were spread evenly across the character set for start point then having the cracker always start at A could be a good choice (you have to start somewhere) but if the spread is not even then a better start choice could be made.
The speeds shown for runs already completed are good, 62M, 69M, 85M hashes per second...
The cracker page also now shows the elapsed time taken.
Dennis has also published proof of concept code for CVE-2009-1979 which was found by him and fixed in the October 2009 CPU. The C code and a binary is available from http://blogs.conus.info/sites/default/files/CVE-2009-1979.zip - (broken link) here. This is the CVSS 10.0 bug on Windows that relates to improper AUTH_SESSKEY parameter length validation.




















